Product Fit and Go-to-Market Strategy
Sense Information
Contents
Differentiated Value Proposition
Identify Distribution Channels
Appendix A – About Personal Data in the GDPR
Appendix B – Public Institutions
Appendix C – Pains of the Public Institutions
Appendix D – Statistics from the Danish data protection agency
Appendix E – Examples of headlines from the media
Appendix F – Sense Information
Appendix H – Value Proposition Questions
Certain details in the following article, are hidden or anonymized.
1 Introduction
Sense Information (the startup) [Appendix F] has built a platform to help organizations prevent data breaches (data loss prevention) that often occur because documents have been stored or distributed wrongfully. The official statistics of data breaches from the Danish data protection agency [Datatilsynet, 2020] confirms the problem. The numbers show that most of the registered breaches come from municipalities and that a majority has to do with information that was sent to the wrong recipient or contained sensitive information [Appendix D].
While the phenomenon of misplaced personal or sensitive information has always been around the organization must now implement suitable measures, due to the introduction of the General Data Protection Regulation (GDPR) in 2018. Appendix A explains some of the paragraphs of the GDPR that are relevant relative to this paper. All data breaches must be registered at the Danish Data Protection Agency which will determine if the organization has not fulfilled its responsibilities of protecting the data. The consequences can be that the organization receives a fine or a warning, or even worse, that the story is published by the media and the reputation of the organization is hurt [Appendix E], [Municipality A, 19:30].
The first release of the product consists of three components, (1) an add-on for the Microsoft Outlook mail client, that notifies the user, if they are about to send an e-mail with personal information, (2) a tool that scans the inbox for e-mails containing personal information, and (3) a website where an administrator can configure policies for which patterns in information the tool should look for, and also provide statistical monitoring of all policy violations in the organization. Sense Information continuously expands the product with the support for multiple communication channels, e.g. Microsoft Teams, Microsoft Sharepoint,, FileShare’s and local PC’s as well as other sources of relevant data.
The purpose of this paper is proposing a product fit and go-to-market strategy for the company. Does the product in fact target what is requested and needed by the market. based on qualitative market research with five public institutions.
2 Market Research
The empirical data research was done by interviewing five public institutions, four municipalities and one university. The interviews were conducted using Zoom and had a duration of 30-60 minutes. The reason to use a qualitative approach was due to the expected complexity and levels of nuances to the answers, another reason was the need to change course depending on the direction of the interview, to explore new hypotheses.
Due to the flexibility of the interviews, the questions were not static, but they were adapted before each interview to also include relevant topics that were brought up in previous conversations. The interviews consisted of four sections, each serving a different purpose, (1) open dialogue to explore the users’ current situation and potential concerns, (2) questioning about their experience with existing solutions, (3) questioning about how they find new solutions to a given problem, and (4) presentation of the product [Appendix F] with the aim of getting their initial feedback.
Anonymized information about the public institutions and the recordings, can be found in Appendix B.
3 Methodology
A go-to-market (GTM) strategy is the plan of an organization, utilizing their inside and outside resources, to deliver their unique value proposition to customers and achieve competitive advantage. In this paper we will propose a GTM strategy by following the five iterative steps, illustrated below, along with a financial plan of the first 36 months.
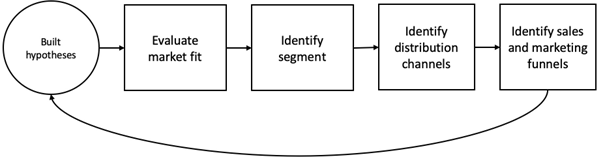
Some of the elements from the GTM strategy are also part of the first two steps, Customer Discovery and Customer Validation, of the Customer Development Model proposed by Steve Blank [Appendix A]. Previous startups have failed, because they neglect to understand the fit between the product and customer needs before launching a product. The model was developed to put an emphasis on learning and discovering facts about the customers, before the execution of building the product, when bringing a new product to market.
The methods and tools used are described in the following sections.
3.1 Effectuation Theory
Saras D. Sarasvathy describe how entrepreneurs navigate through uncertainty by using a special type of reasoning during decision making called Effectuation theory. The theory describes that when decision makers believe they are dealing with a measurable or relatively predictable future, they will tend to do some systematic information gathering and invest some effort on a reasonable analysis of that information, within certain bounds. Similarly, if they believe they are dealing with relatively unpredictable phenomena, they will try to gather information through experimental and iterative learning aimed at first discovering the underlying distribution of the future [Sarasvathy, p. 252].
The approaches by Blank[Blank, 2020] and Ries[Ries, 2011] are also founded on effectuation theory and describes how to use hypotheses or a Minimal Viable Product (MVP) to validate the assumptions of the business model.
As we have described in the Market Research section, the approach for this research has been to make hypotheses about the potential users and test them for each interview. However, effectuation theory is involved in many sections through out the paper.
3.2 Jobs to be Done
Clayton M. Christensen describe why it is important to understand what a customer seeks to accomplish in each circumstance when building customer profiles, in what he calls the theory of jobs to be done [M. Christensen et. al., 2016, p. 2]. The circumstances are more important than looking for correlations in data as e.g., customer characteristics, product attributes, new technologies, or trends, because jobs are never simply about function, but have powerful social and emotional dimensions [M. Christensen et. al., 2016, p. 7]. We are therefore using jobs to be done theory to understand the needs of the prospect customers.
3.3 Value Proposition
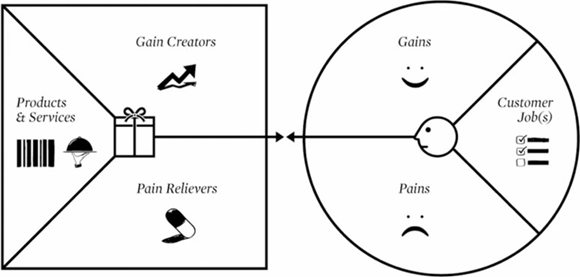
A value proposition answers the question of why a customer should buy a particular product or service. We are using the Value Proposition Canvas (VPC) to identify the value proposition by mapping the customers pains and gains identified by jobs to be done theory, with the gain creators and pain relievers the startup is offering through the differentiators of their products and services. The fit between the two parts, is used to define the value proposition.
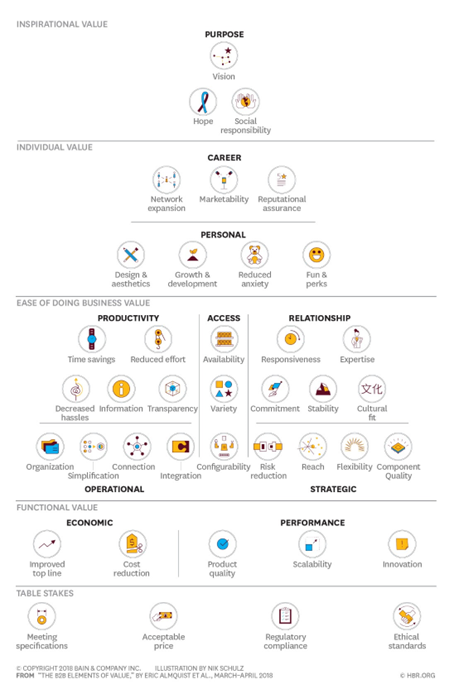
From their research Almquist et. al. identifies 40 fundamental “elements of value”, that fall into five categories: table stakes, functional, ease of doing business, individual, and inspirational [E. Almquist et al., 2018]. The elements of value allow managers to identify what matters most to each set of important stakeholders and how the company can stand out from the competitive pack. The elements are sorted into the levels of a pyramid, with those providing more objective value at the base and those that offer more subjective value higher up [Appendix G]. The battle to differentiate is shifting towards the more emotional elements at the middle and upper levels, that have traditionally been difficult to isolate and quantify.
3.4 Segmentation
Moore describes the technology adoption life cycle as a bell curve representing the thesis that technology is absorbed into any given community in stages corresponding to the psychological and social profiles of various segments within that community [Moore, 1991, p. 10].
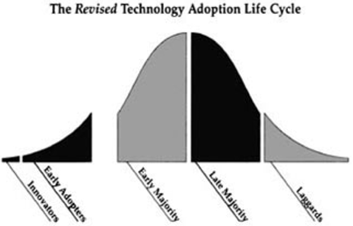
The model is split in five community segments, (1) innovators pursue new technology aggressively, (2) early adopters buy into new product concepts early, (3) the early majority are driven by a strong sense of practicality and want to see well-established references, (4) the late majority shares concerns with early majority but are not comfortable with handling technology, and (5) laggards are people that simply do not want anything to do with new technology. Between each segment there is a gap that represents an opportunity for marketing to lose momentum [Moore, p. 12].
3.5 The Resource Based View
Srivastava et. al links the resource-based view with marketing in their framework for analysis of market-based resources, as a continuous process of exploring new opportunities to achieve long-term competitive advantage, as opposed to exploiting existing opportunities [Srivastava et. al., 2001, p. 788]. The opportunities are intangible resources known as market-based assets and capabilities, that can have an external focus from the company, e.g., building relationships with customers and networks, or internal focus based on intellectual knowledge embedded with the individuals and processes of the company.
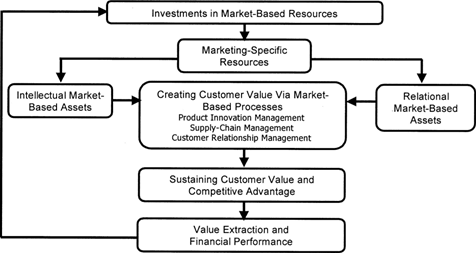
To sustain competitive advantage, the company must be able to generate customer value from the identified market-based assets and capabilities, by focusing on resources that are valuable, rare, inimitable, and nonsubstitutable (organization), also defined as the VRIO framework [Srivastava et. al., 2001, p. 790].
3.6 The Marketing Funnel
The marketing funnel illustrates the hypothetical journey a customer takes when going from a stranger to a customer. The classic marketing funnel has five stages, (1) Awareness, (2) Interest, (3) Evaluation, (4) Trial, and (5) Adoption, which are a series of interactions between people and the company. People will be interested in different information according to their location in the funnel [Management, 2017]. We will describe which activities and metrics that are relevant to implement at each stage of the marketing funnel.
4 Evaluate Market Fit
In this section we will evaluate the market fit by examining the value proportion of the product. In order to define the true value of the product, the customer profiles must be well understood by first conducting a jobs to be done analysis.
4.1 Jobs to be Done
The main driver of the jobs to be done are that the institutions want to ensure compliance with the GDPR, to keep a good reputation and prevent them from being fined by the Danish data protection agency due to violations.
The presented product is aimed at two groups of users within the public institutions, that have different jobs to be done, (1) Data Protection Officers (DPOs) with the interest of ensuring compliance with the GDPR in the organization, and (2) employees that want to communicate with their clients and users as part of their work, while following guidelines and policies in order to make sure that their own work is compliant with the GDPR. In the following sections We will cover the jobs to be done by the two customer profiles.
4.1.1 Data Protection Officers
In general, the role of the DPO is defined by the GDPR [GDPR, 2020] where it is also stated that all organizations that processes personal information must have one. The jobs to be done by the DPO are three-fold, the DPO is responsible for (1) educating the organization about compliance, (2) training employees involved in data processing, and (3) conducting regular security audits.
None of the representatives we talked with had sufficient tooling to perform comprehensive security audits, which would often be based on a sample, or the number of violations registered by the employees. One DPO also mention the concern that not all employees may be well enough informed to identify when a violation occurs [Municipality B, 25:00]. They all agreed however, that they were sure violations existed, they simply did not have the means to identify them. Several of the DPOs told that their experience with existing tools on the market, are that they are not mature enough to identify violations accurately or provide them with sufficient information about the violations [Municipality C, 9:00], [University A, 19:30].
The DPOs do not have any authority or resources themselves but must find support from upper management or the councils within the municipality [Municipality D, 4:20]. Without a method to effectively monitor violations, it can be hard to justify the prioritization of resources to the area.
4.1.2 Employees
The employees of the public institutions can have many different functions, from case workers at the job center to childcare workers at a kindergarten.
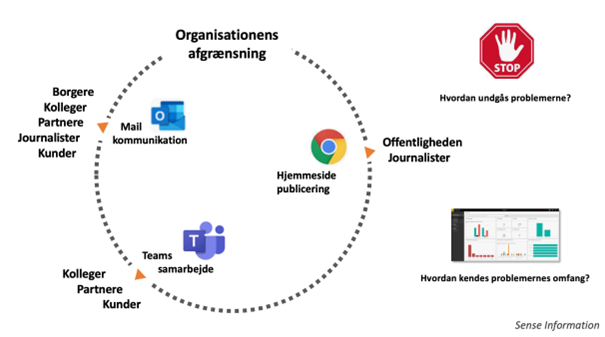
One job they have in common, is that they often at some point will have to communicate with citizens or users about personal matters by e-mail. Depending on their function, communication by e-mail will more or less be an integrated part of their work. The employees are obliged to follow policies in the form of guidelines set by the DPO, to ensure GDPR compliance, when sending, receiving, or storing e-mails with personal information. The policies involve that communication must be done using an encrypted communication protocol, e.g., Digital post, and that the e-mails are not stored for more than 30 days or if there is a legal basis [Municipality D, 9:30].
The workflow for sending or receiving an e-mail is described by the following illustration:
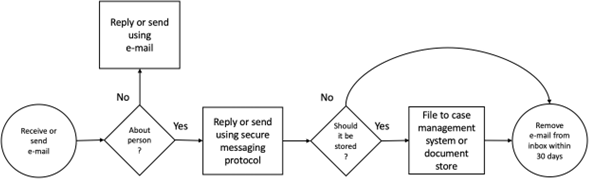
The employees therefore have the following jobs to be done, (1) communicate with their clients and stakeholders through e-mail and other communication channels, (2) communicate using secure channels when information is personal, (3) move old messages from personal devices to a secure shared document store.
From the customer pains identified in the VPC in the following section, it is revealed that many of the errors occur because the employees continually must evaluate when and what to do, while still relate to the content of the e-mail. The process of sending and receiving e-mails are perceived as cumbersome by the employees [Municipality A, 4:00], and it often leads to frustrations when policy violations occur [University A, 54:00].
4.2 Value Proposition
The jobs to be done analysis describe two customer profiles with two separate but related problem areas. To evaluate the fit between the product gains and the pains of the two customer profiles, a VPC for each of the two is analyzed in this section. A comprehensive list of the identified pains from the empirical research can be found in Appendix C.
4.2.1 Data Protection Officer
4.2.1.1 Products and Services
- Insights into problematic areas in the organization
- Easy setup and installation
- Options for running the solution as a SaaS or on-premise
Pain Relievers
- Identify and prevent data breaches
- Central monitoring in real-time
- A head of compliance
- Fear of negative exposure by other authorities or media
- Data do not have to be hosted in the cloud
Gain creators
- Reduce resources used on education and campaigns
- Reduce time spend on registration and handling of policy violations
- Positive image of the organization
4.2.1.2 Customer Profile
- Educate organization about compliance
- Train employees about compliance
- Perform regular security audits
Pains
- We lack the insights to know where to focus our attention in order to improve compliance
- We use multiple communication channels which make it harder to monitor and control violations, e.g., SMS and Microsoft Teams.
- Existing products have too many false positive policy violations which takes many resources to go through and identify.
- Existing products are often expensive and take a lot of time to install and configure.
- We cannot use new cloud-based solution due to the American Cloud act
Gains
- Better prioritization of resources
- Reduce the costs and resources used in education
- Reduce the cost and resources spend on periodically clean-up campaigns for all staff
4.2.2 Employees
4.2.2.1 Products and Services
- Notify employee of compliance problems
- Easy and intuitive to use
- Central configuration by an administrator
Pain Relievers
- Instant notification to user if e-mail contains personal information
- Prevents data breaches before they occur
- No need for education or training in using the tool
Gain creators
- Employee can focus on their primary work tasks
- Reduce number of data breaches
- Reduce resources spend on education and training in compliance
- Reduce time spend on manual tasks
4.2.2.2 Customer Profile
- Communicate with citizens about personal matters
- Receive training in compliance
- Take part in regular “clean-up” campaigns
Pains
- Most data breaches occur due to human error. The most common are e-mails containing personal information or personal information that is send to the wrong receiver.
- Workflows are becoming more complex because they are extended to include verification steps to prevent data breaches
- Campaigns to clean-up inboxes are time consuming and tedious
- It is frustrating for the employee when a data breach occurs
Gains
- Reduce number of data breaches
- No more annoying and time-consuming manual tasks to identify policy violations
- Can focus on their work
- Reduction of time spend on handling e-mails
- Reduce time spent on education
- Reduce frustration
By examining the fit between the product and the two customer profiles of the VPC it is confirmed that the product provides value to the potential customers.
4.2.3 Elements of Value
To identify the value elements that are most important, Almquist et. al. proposes five steps, (1) benchmark the value proposition against the competition, (2) talk with customers, (3) imagine ways to increase value by identifying new elements to focus on, (4) refine, test and learn, and (5) apply the acid test by re-evaluating the benchmark ideally by rerunning the original research [E. Almquist et. al., 2018].
The current product attributes can be categorized into the following five value elements, that belong to the three bottom stages of the value pyramid [Appendix G]:
Regulatory compliance (Table stakes): The product helps its customers to become GDPR compliant
Risk reduction (Strategic): The product reduces the risk of data breaches.
Cost reduction (Economic): Reduces costs on education and compliancy campaigns
Transparency (Productivity): Increases transparency by monitoring files with personal information (policy violations)
Time savings (Productivity): Simplification of work processes, due to less time spent on manual processes
Emotional value elements that the startup can try focusing on to differentiate themselves from the competition and gain a competitive advantage are:
Reputational assurance (Career): Make it import for the individual employee to reduce the number of violations that they are responsible for, e.g., by comparing the number of their violations with their peers.
Social responsibility (Purpose): Data breaches can have serious consequences for the individual person whose data has been leaked. Can we make it a personal motivation for the employee to reduce the number of policy violations, e.g., by showing them how many data breaches they have prevented?
4.2.4 Differentiated Value Proposition
To clearly communicate the competitive advantage and the value the product brings to market in a precise value proposition; We use the differentiated value proposition framework. The framework is not founded in research but has been developed and used by Implement Consulting [Implement, 2020].
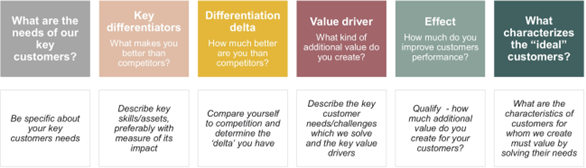
By answering the six questions of the differentiated value proposition framework [Appendix H], We can formulate the value proposition in the following sentence:
We help public institutions reduce data breaches in their communication with citizens about personal matters, due to our real-time policy violation identification tool which is more accurate than existing tools on the market.
5 Segmentation
In general, the public institution can be regarded as technologically mature, because they already rely on many software solutions to carry out their core business processes. However, several of them are risk averse, and are only interested in using solutions that have a proven track record at other public institutions. Experience with private companies is not as reliable, because they do not share the same matter of issues as public institutions [Municipality 4, 18:30].
Some of the concerns of having a startup as a provider, is whether they have the resources to provide sufficient customer service, and the experience to build a product that has a high level of security [Municipality A, 18:30]. However, two of the institutions expressed that they are willing to take on more risk with this product, because they perceive it as a tool to support their work, and it does not constitute a risk to their core business processes [Municipality B, 1:02]. One institution already had a collaboration with a small company which they were positive about, because it gave them the possibility of influencing the product and thereby customizing it to their own needs [Municipality #, 26:00].
5.0.1 Positioning
According to Moore you should cross the chasm by targeting a very specific niche market where you can dominate from the outset, force your competitors out of the market niche, and then use it as a base for broader operations [Moore, 1991, p. 49].
The startup should therefore focus on those public institutions that are willing to initiate in a close collaboration to make a track record of public institutions that can be used to create a track. During the collaboration, the startup should be aware of avoiding the innovator’s dilemma [Henderson, 2006], where they end up only catering for their existing customers instead of exploring new innovations.
6 Identify Distribution Channels
Based on the segment analysis the chosen distribution channels must depend on creating close relationships with prospect buyers, that can continue after a purchase.
Because the product is complex, it is also expected that the purchase decision requires high involvement and more effort. High involvement products are generally expensive, rarely, or infrequently purchased and usually involve some form of risk, such as financial or social risk. Where the risks are high the consumer is more likely to devote time and effort to careful consideration of alternatives before making a purchase [Bewsell and Brown, 2009, p. 82].
The proposed distribution channel is therefore using direct sales, that can facilitate and support the prospect customer during a purchase.
It may also be relevant for the startup to pursue a collaboration with another company, to gain a collected competitive advantage. We will examine this in the next section using the resource-based view.
6.1 The Resource Based View
We use the VRIO framework to analyze the startup’s resources and identify if they lack any market based assets.
Value: The product provides value by preventing data breaches from public institutions which was examined in the value proposition section.
Rarity: Similar products are already available on the market, but they work by asynchronously scanning files for patterns. A scan is time consuming and will often only be run once a month [Municipality C, 8:30]. A scan will have to be followed by an extensive cleaning-exercise, where the users will have to go through all the findings and deal with the violations manually [University A, 12:00].
The features that are unique to the product, is that it offers real-time monitoring of policy violations on multiple communication channels. The product is integrated into the communication client, e.g., Microsoft Outlook, and can therefore provide the user with instant feedback based on the users input before the message is send.
The concept of identifying personal information in files is therefore not unique to the market, however, the combination of features is.
Imitability: It will require knowledge about the problem area and technical know-how to imitate the product. Although this is not common knowledge, it is relatively easy to obtain it or to hire people with the appropriate knowledge and experience within the relevant fields. The product will therefore only temporarily be safe from being imitated.
Organization: It’s founder, has many years of experience within the field, from working with a similar category product at a competing company [Appendix J]. The market-based assets therefore consist of the intellectual and relational assets he has, in the form of knowledge about the environment, technical know-how and relationships to potential customers and partners. However, organizational structures to facilitate the continuous exploration and generation of resources, is needed to secure that the startup has a competitive advantage in the long run.
My findings from the VRIO analysis show that the startup must start building an organization of knowledgeable employees, that can continuously scan and explore the environment for new opportunities and resources and expand their market-based assets, to keep developing the product and ensure that it is safe from being imitated in the long run.
6.2 Partnerships
The startup also has the possibility of using partnerships to exploit the market-based assets of an established company within a related field. The empirical research confirmed that the problem of identifying personal information is not only relevant for e-mails, but also for other communication channels and for documents stored in document- and case management systems.
A possible partner could therefore be found among the case management providers that could bundle the product with their solution, based on a licensing agreement. The incentive for the case management providers is to increase their competitive advantage on the market by providing an overall better product for their customers. From the interviews we learned that other case management systems, already has similar functionality built-in [Municipality 2, 27:00], which should constitute as a competitive thread for those providers that have not managed to implement the technology themselves.
7 Sales and Marketing
Based on the empirical research the startup should base their strategy primarily on inbound marketing by building lasting relationship with prospects and customers, due to the following facts, (1) the early adopters identified in the segments analysis want to initiate in close collaborations in order for them to influence the product to their needs, (2) the public institutions are constantly contacted by sales personnel by phone or e-mail which in general never lead to a sale [Municipality 2, 44:00], (3) their decision making are mostly affected by what they hear through word of mouth from other public institutions [Municipality 2, 44:00], [Municipality 1, 14:30].
The strategy will not purely be based on an inbound strategy, as outbound methods is used in the early stages of the marketing funnel, to achieve a broader reach through paid advertising.
7.0.1 Marketing Funnel
In the following sections, the activities and metrics, at each stage, in the marketing funnel, are described. The metrics must continuously be collected and analyzed, to gain information about the quality of the interactions with the prospect customers and adjust the activities to improve the conversion rate.
Awareness:
As discussed earlier, the decision making of the prospect customers are mostly based on experience (a track record) and word of mouth, and it is therefore important to position the startup as an expert within the field.
The startup should use inbound content marketing methods as e.g., blogs, articles, webinars, and conferences, to share their knowledge within the field of GDPR compliance and data loss prevention, and their experiences with the product. The content is published on the startup’s own website and on social media, and it is shared by organic and paid promotion (outbound) to achieve a better reach. Experiments with Search Engine Optimization (SEO) should also be conducted at this stage, in order to increase the traffic to the website by making sure that prospect customers can find it.
They can also target smaller blogs with communities within the same niche. There are different tactics to target blogs, e.g., using a search engine or Twitter to find related content, or simply by asking people [Weinberg and Mares, 2015, p. 46]. However, they should be aware that disclosed sponsored content have repeatedly shown to be perceived less favourably by the prospect customers [Müller and Christandl, 2019, p. 53]. Like blogs, webinars can be held at other communities or in partnership with others that share the same niche.
| Activities | Metrics to track |
|---|---|
| Blog posts and webinars | Website traffic |
| SEO optimization | Social media reach and interactions |
| Paid and organic reach through social media Find related communities to collaborate with | Shares |
Interest:
A prospect customer can show interest by following the startup on social media or signing up for a newsletter to receive information about future blog posts and webinars. At this point the aim is to nurture and build the relationship, by continuously providing the potential customers with relevant information and give them opportunities to interact with the company [Skyword, 2020].
From the empirical research, conferences about public digitalization, e.g., OffDig [DanskIT, 2021], were repeatedly mentioned as a place where the potential customers would collect information about new technologies and share experiences with their colleagues from other municipalities [Municipality 3, 23:30]. Conferences can both be used to create awareness about the product and be a place to meet interested prospect customers.
The startup should therefore attend conferences by having a booth to meet prospect customers in person, but also attend as a public speaker to create awareness. Research suggest that in-person events do not have a significant effect on lead generation compared to digital events [Wang et. al., 2017, p.167], attendance at conferences should therefore not be preferred over digital events like webinars.
| Activities | Metrics to track |
|---|---|
| Promote events through social media and newsletters | Event signups |
| Attend meetups and conferences | E-mail open rates Social media reach and interactions |
Evaluate:
At this stage the prospect customer will be interested in learning about the product to make a decision of whether to make a buy. It is therefore important that the information about the product is available for the prospect customer, to base their decision upon.
Product information must therefore be available at the company webpage along with contact information to a salesperson for an informal conversation about the product.
| Activities | Metrics to track |
|---|---|
| Build product page | Website traffic |
| Offer demo and free 30-day trial Offer informal conversation with salesperson | Number of leads |
Trial:
The prospect customer will try out the product for free in a 30 days trial period. As mentioned in the segment analysis, the public institutions expect a high quality in customer service. Therefore, the startup must provide support, e.g. in the form of tutorials, FAQs and contact information to customer service.
| Activities | Metrics to track |
|---|---|
| Offer customer service Offer tutorials and FAQs | Lead-to-sale conversion rate |
Adoption:
The customer has now been upgraded to a paid plan. At this stage it is important to provide ongoing customer service to increase customer loyalty in order to increase the customer lifetime value [Autopilot, 2020].
As previously mentioned, the results from the empirical data show that word of mouth has the most significant impact on the purchase decision-making of the prospect customers. The final stage in the Pirate Funnel presented by Dave McClure, is the referral stage [Grow with Ward, 2021]. At this stage we want make customers make referrals to others using word of mouth, e.g. by sharing their experience on social media or make them invite a friend for a free upgrade.
The startup also has other related products in their pipeline, that they would want to sell to their existing customers, using the same methods as during the Evaluate stage.
| Activities | Metrics to track |
|---|---|
| Run referral contests | Number of referrals |
| Offer free upgrade for a limited period | Number of upgrades |
8 Financial Plan
The financial plan is calculated from estimates over a period of 36 months, and covers the sales of three products, (1) the initial MVP which is the GDPR compliancy solution for e-mails covered in this paper, and two products that builds on the same foundation as the MVP which is, (2) GDPR compliancy for the Office 365 package, and (3) GDPR compliancy of case management systems [Appendix I].
The products are estimated to be released six months apart. The different products are sold as subscription plans and can therefore be sold to the same customers. Although the public institutions are the initial targets, they also expect to move into the private sector.
Because the marketing strategy is primarily based on inbound content marketing, the most expensive initial costs are salaries for sales, marketing, and customer support personnel in order to build content and create relationships with the customers. Webhosting, paid promotion (average) cost, and free trial (average) costs are included as fixed costs.
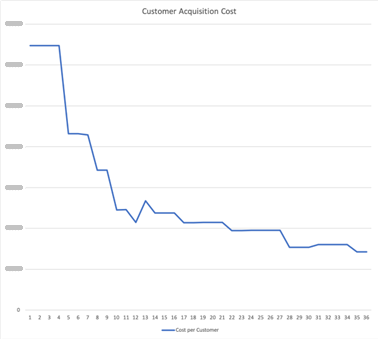
The diagram show that the customer acquisition cost (CAC) is very high at the beginning, but quickly falls as the number of customers increases, until the cost per customer is approx. #,- per month.
It is hard to make a qualified estimate of the customer lifetime without any initial metrics to build this on. For this reason, the customer lifetime is set to an average of 24 months. The customer lifetime value (CLV) using one subscription plan is #,- while the CLV for a customer on three plans is #,- which is a significant difference.
Although a CLV of #,- seems reasonable for an CAC of #,-, it is only viable in the long-run due to the initial costs of building relationships and on-boarding new customers. Within the period of 36 months, the monthly costs will never break even, with the earnings of customers on only a single subscription plan, which is shown in the plot below.
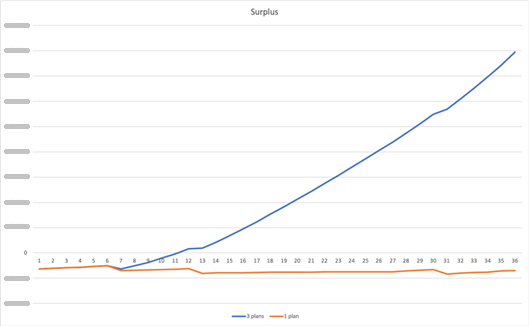
However, if the startup is able to sell the new subscription plans to existing customers, the earnings will outset the costs after 11 months. Therefore, it is important for the startup to develop its portfolio of related products, that they can sell to their existing customers.
References
[Almquist et al., 2018] Almquist, E., Cleghorn, J., and Sherer, L. (2018). The b2b elements of value. Harvard Business Review.
[Autopilot, 2020] Autopilot (2020). The marketing funnel explained from top to bottom. https://journeys.autopilotapp.com/blog/marketing-funnel-explained/. accessed 06-14-2021.
[Bewsell and Brown, 2009] Bewsell, D. and Brown, M. (2009). Involvement and decision making on-farm: the use of wintering feedpads and nitrogen inhibitors on dairy farms in new zealand.
[Blank, 2020] Blank, S. (2020). The Four Steps to the Epiphany: Successful Strategies for Products that Win. Wiley, 5 edition.
[DanskIT ,2021] DanskIT (2021). Offdif-2021. https://www.dit.dk/da/Konferencer/OffDig2021/Om-konferencen. accessed 06-14-2021.
[Datatilsynet, 2020] Datatilsynet (2020). statistik over anmeldte brud. https://www.datatilsynet.dk/sikkerhedsbrud/statistik-over-anmeldte-sikkerhedsbrud. accessed 06-14-2021.
[GDPR, 2020] GDPR (2020). Article 37. https://gdpr-info.eu/art-37-gdpr/. accessed 06-14-2021.
[Grow with Ward, 2021] Grow with Ward (2021). Aaarrr pirate funnel. https://growwithward.com/aaarrr-pirate-funnel/. accessed 06-14-2021.
[Henderson, 2006] Henderson, R. (2006). The innovator’s dilemma as a problem of organizational competence.
[Implement, 2020] Implement (2020). Value proposition playbook. https://implementconsultinggroup.com/value-proposition-playbook/. accessed 06-14-2021.
[Management, 2017] Management, E. P. (2017). understand-the-marketing-funnel. https://expertprogrammanagement.com/2017/06/understand-the-marketing-funnel/. accessed 06-14-2021.
[Moore, 2001] Moore, G. A. (2001). Crossing the Chasm. Perfect Bound, revised edition.
[Mu¨ller and Christandl, 2019a] Mu¨ller, J. and Christandl, F. (2019a). Content is king – but who is the king of kings? the effect of content marketing, sponsored content user-generated content on brand responses. Computers in Human Behavior.
[Mu¨ller and Christandl, 2019b] Mu¨ller, J. and Christandl, F. (2019b). Content is king – but who is the king of kings? the effect of content marketing, sponsored content user-generated content on brand responses. Computers in Human Behavior.
[Ries, 2011] Ries, E. (2011). The Lean Startup. Currency, 1 edition.
[Skywords, 2020] Skywords (2020). How the marketing funnel works from top to bottom. https://www.skyword.com/contentstandard/how-the-marketing-funnel-works-from-top-tobottom/. accessed 06-14-2021.
[Srivastava et al., 2001] Srivastava, R. K., Fahey, L., and Christensen, H. K. (2001). The resourcebased view and marketing: The role of market-based assets in gaining competitive advantage.
[Wang et al., 2017] Wang, W.-L., Mathouse, E. C., Calder, B., and Uzunoglu, E. (2017). B2b content marketing for professional services: In-person versus digital contacts. Elsevier Inc. [Weinberg and Mares, 2015] Weinberg, G. and Mares, J. (2015). Traction: How any Startup can Achieve Explosive Customer Growth. Penguin Business, 5 editions.
9 Appendix A – About Personal Data in the GDPR
According to article 9 in the GDPR an organisation is in general prohibited from collecting and storing, special categories of personal data, also referred to as sensitive personal information, unless one of ten conditions apply:
”Processing of personal data revealing racial or ethnic origin, political opinions, religious or philosophical beliefs, or trade union membership, and the processing of genetic data, biometric data for the purpose of uniquely identifying a natural person, data concerning health or data concerning a natural person’s sex life or sexual orientation shall be prohibited.”(art. 9)
Due to the conditions, it is primarily public institutions and authorities that have legitimate reasons to process sensitive personal information.
The institutions also have to comply with the general principles described in article 5 of the regulation, where the principles of data minimisation and storage limitation are of special relevance. About storage minimisation it is stated that data should only be stored when and where there is a legitimate purpose:
“Personal data shall be collected for specified, explicit and legitimate purposes and not further processed in a manner that is incompatible with those purposes…” (art. 5(1)(b)).
To comply with the principle of storage limitation, the organisation must not keep personal data that permits identification of data subjects, for longer than is necessary for the purposes of the processing (GDPR art. 5(1)(e)).
10 Appendix B – Public Institutions
| Institution | Name | Job title |
|---|---|---|
| Municipality 2 | — | — |
| Municipality 1 | — | — |
| Municipality 3 | — | — |
| Municipality 4 | — | — |
| University 1 | — | — |
11 Appendix C – Pains of the Public Institutions
| Pains for the Municipality # |
| Folk vil ikke bruge eBoks. |
| Der er ikke en sikker på at have direkte kontakt med borgerne på. |
| Der må ikke være personfølsomme oplysninger i SMS, bl.a. i kommunikationen med unge. |
| Det er okay at benytte andre medier end eBoks, så længe det ikke indeholder personfølsomme oplysninger. Men det bevæger sig hurtigt ind på områder, hvor der er noget personfølsomt. |
| Mails med personfølsomt indhold må ikke ligge i indbakken i mere end 30 dage. |
| Den nuværende løsning med skanning af e-mails for CPR-nummer, giver alt for mange falske positive, som det tager tid at rydde op i. |
| De kan ikke finde en løsning til at skanne efter andet end CPR-nummer, som f.eks. helbredsoplysninger. |
| Mail sendes til for mange, pga. kultur med at sætte mange CC på mails. De forsøger at løse dette med en kulturændring. |
| Medarbejderne kommer også til at sende mails forkert, og derved deles personfølsomme oplysninger uhensigtsmæssigt. |
| En løsning skal kunne sættes op centralt for alle medarbejdere, så det ikke er noget man opdager er ”slået til”. |
| De samme problemstillinger for e-mails, gælder ogs˚a for Microsoft Teams. |
| Pains for Municipality # |
| Sagsbehandlerne synes det er besværligt at bruge Digital Post. |
| Det tager længere tid at sende post via eBoks, det tager ca. et døgn. |
| De fleste brud på datasikkerheden er fordi at e-mails sendes til alm. private adresser (ukrypterede). |
| Nogle borgere kan man kun kommunikere med over SMS, f.eks. udsatte unge. (ikke sikker kanal). |
| Det er svært at ændre på gamle vaner (kultur), mange har e-mails liggende der aldrig bliver ryddet op i. |
| Det er en bekymring for DPO og jura at der skulle komme kritik fra Datatilsynet i forbindelse med et eftersyn. |
| Der er brugt to år på at komme i gang med at bruge en løsning til skanning af bl.a. indbakker (lang installation). |
| De ved at der er et problem, men de kender ikke det egentlige omfang af problemet. |
| De oplever løbende at der sender e-mails til forkerte modtagere med personfølsomt indhold. |
| Lige nu er der ikke en sikker måde at bruge chatfunktioner lovligt, da data opbevares i et ”usikkert” tredje land (USA). |
| Pains for Municipality # |
| Den største bekymring er menneskelige fejl. Det man ser mest er at medarbejderne taster forkert, f.eks. vælger en forkert modtager af en mail. |
| De fleste kommuner har erfaringer med at der ligger informationer i indbakker, som hverken er journaliseret eller slettet. |
| De har ikke mulighed for at foretage kontrol. De foretager stikprøver fra drev, men må kun foretage stikprøver fra en medarbejders indbakke, hvis der er en begrundet mistanke. |
| Problemet er større jo længere væk fra rådhuset man kommer. Der er medarbejdere i kommunen som hare sværere ved at følge retningslinjerne, fordi at de sidder alene og ikke har fået den nødvendige sidemandsoplæring. |
| Et stort problem er at man betaler for en løsning for en periode på fem år, hvorefter man finder ud af at man ikke har brug for den efter to år. |
| Pains of University # |
| Det er ikke altid muligt at benytte eBoks og andre kanaler må derfor tages i brug. |
| De har hørt fra andre institutioner, hvor skanning af medarbejdernes indbakker ikke er effektive, fordi der er for mange falske positive, som de skal rydde op i bagefter. Det giver dobbelt så meget arbejde. |
| Oprydning af e-mails foregår ved at udføre manuelle oprydningsøvelser |
| Det er ikke muligt at overvåge om oprydningen er effektiv, da de kun undersøger ændringer i mængden af mails. |
| Skanninger alene vil ikke gøre arbejde lettere, da meget af arbejdet handler om at kommunikere med afdelingerne om generel procedure og oprydning. Det er vigtigt for ham at han kan bibeholde kommunikationen for at vedligeholde de gode relationer. |
| Det er ikke muligt at skanne efter CPR numre eller helbredsoplysninger da det vil give for mange falske positive, med de nuværende løsninger der er på markedet. Produkterne er ikke modne nok. |
| Det er en afvejning af risikoen for at der slipper personfølsomme oplysninger ud og økonomi. Ingen har ryddet op i det hele. |
| Den primære grund til at de oplever at personfølsomme oplysninger ”slipper ud”, er fordi at en e-mail sendes til den forkerte modtager. |
| Medarbejdere er ikke bange for at begå fejl, men de bliver frustrerede når det sker. |
| Pains for Municipality # |
| Vi bryder os ikke om e-mails da de kræver visitering af flere medarbejdere, før de når den rigtige modtager, og det er dyrt. Vi får nogle hundrede mails ind om dagen. |
| Det er et problem at medarbejdere journaliserer oplysninger om kommunikation via e-mail, da andre medarbejdere ikke får denne information. |
| Vi ved ikke hvor stort problem med personfølsom information i e-mails er, det måler vi kun ift. de brud der registreredes hos databeskyttelsesrådgiveren. |
| De fleste brud der registreres, går på at kommunikation er foregået på en ikke-sikker kanal. |
| Vi modtager jævnligt registreringer på brud på datasikkerheden pga. personfølsom information i e-mails. |
| Vi har ikke foretaget en skanning af e-mails for personfølsomt indhold, selvom vi har muligheden for det. Det skyldes at vi ved at problemet er der, men det kræver tid og energi at f˚a medarbejderne til at gøre noget andet end de plejer (kulturændring). |
| Det er ikke altid at brud på datasikkerheden registreres, derfor er det svært at kende omfanget af problemet. |
| Det er et problem med information som er registreret forkert på sager. F.eks. hvis en e-mail med personfølsomt indhold er journaliseret på en sag, og personen ikke er registreret som part på sagen. |
| Det er en bekymring at ledere og medarbejdere ikke får registreret brud på datasikkerheden, fordi de ikke ved hvornår at der er et brud (at uddannelsen ikke har været tilstrækkelig). |
| Det er en bekymring at ledere og medarbejdere ikke får registreret brud på datasikkerheden, fordi de ikke ved hvornår at der er et brud (at uddannelsen ikke har været tilstrækkelig). |
| Der findes jævnligt personfølsomme oplysninger i byggesager som de har publiceret offentligt. Nogle gange er det borgerne selv der henvender sig for at få fjernet oplysningerne. |
| 95% af fejl er menneskelige fejl, som f.eks. at e-mails sendes til den forkerte modtager. |
| De har forsøgt at ændre procedurerne i arbejdsgangene, så medarbejderen manuelt skal foretage et tjek af CPR-nummeret, inden en mail afsendes. Men det er besværligt. |
12 Appendix D – Statistics from the Danish data protection agency
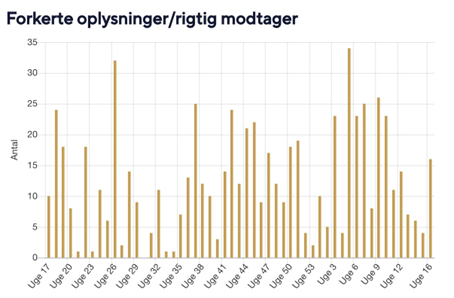
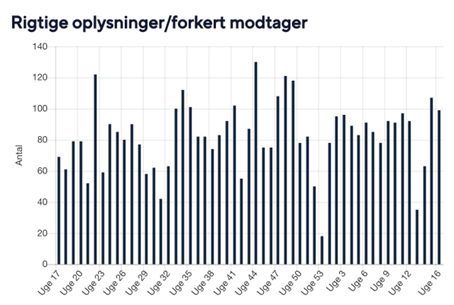
13 Appendix E – Examples of headlines from the media
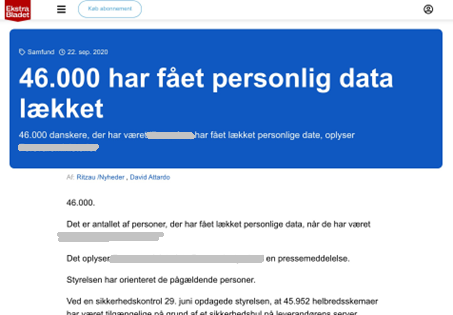
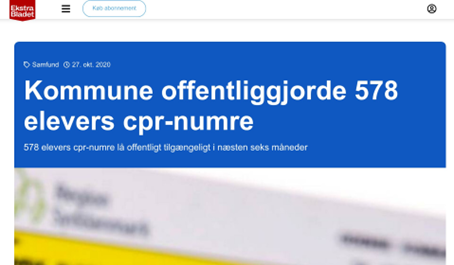
14 Appendix F – Sense by Sense Information
15 Appendix G – Value Elements

16 Appendix H – Value Proposition Questions



Comments are closed